It is straightforward to produce and configure new SSH keys. Inside the default configuration, OpenSSH permits any person to configure new keys. The keys are long term entry credentials that stay valid even after the user's account has been deleted.
3. The following prompt would be the passphrase, that may be left blank. Alternatively, set a passphrase to secure your important by necessitating a password Each time it is actually accessed.
This article has delivered three methods of producing SSH essential pairs on a Windows technique. Utilize the SSH keys to hook up with a distant method without the need of making use of passwords.
The utility will prompt you to pick out a location for that keys which will be produced. By default, the keys will likely be stored from the ~/.ssh Listing inside of your consumer’s home directory. The private crucial will likely be called id_rsa along with the associated public critical will be named id_rsa.pub.
These are requested for his or her password, they enter it, and they're linked to Sulaco. Their command line prompt changes to confirm this.
The private critical is retained through the consumer and may be kept Certainly magic formula. Any compromise with the private vital allows the attacker to log into servers which have been configured Together with the associated community critical with out added authentication. As yet another precaution, The true secret is usually encrypted on disk having a passphrase.
The algorithm is selected utilizing the -t possibility and important measurement utilizing the -b option. The following commands illustrate:
We at SSH protected communications among units, automated apps, and other people. We strive to develop long term-evidence and safe communications for firms and corporations to expand properly within the digital earth.
While you are prompted to "Enter a file during which to save lots of The important thing," push Enter to simply accept the default file place.
Some familiarity with dealing with a terminal and the command line. If you need an introduction to dealing with terminals and the command line, you are able to pay a visit to our guidebook A Linux Command Line Primer.
This is how to make the many SSH keys you will ever will need utilizing 3 unique methods. We'll demonstrate ways to produce your initial set of keys, along with added ones in order to generate unique keys for a number of web sites.
To implement community key authentication, the general public important have to be copied into a server and installed within an authorized_keys file. This createssh may be conveniently accomplished using the ssh-copy-id Software. Such as this:
Safe Shell (SSH) is a way for creating a protected connection amongst two desktops. Vital-based authentication employs a vital pair, Using the personal key on a remote server and the corresponding public important on a neighborhood device. Once the keys match, accessibility is granted to your distant consumer.
Step one to configure SSH critical authentication on your server should be to crank out an SSH crucial pair on your neighborhood Laptop.
 Ariana Richards Then & Now!
Ariana Richards Then & Now! Jason J. Richter Then & Now!
Jason J. Richter Then & Now!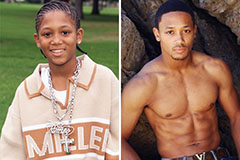 Romeo Miller Then & Now!
Romeo Miller Then & Now!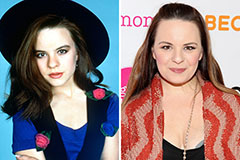 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Barbara Eden Then & Now!
Barbara Eden Then & Now!